Yes, with Posteo, every access occurs encrypted. This happens regardless of whether you use Posteo via the webmail interface, with local email programs or mobile devices: Access to your account (on our servers) occurs fundamentally over encrypted TLS connections. We additionally secure these connections with “Perfect Forward Secrecy” (PFS) technology and with DANE/TLSA. PFS actively prevents that any potentially recorded connection information could be mass-decrypted by third parties. DANE verifies the validity of our servers. In every environment, you can then be sure that nobody is spying on network traffic between you and Posteo, reading your emails or stealing your access information.
Why we encrypt access
These days, users access their email through a variety of means – for example, over open Wi-Fi networks or internet cafés. If log in occurs unencrypted, third parties can easily obtain your access information. In some circumstances, they can thereby access not only your emails, but also your login details for other online services. Because many users have set up similar passwords and usernames with various sites, a back-door is opened as soon as access to an email account is established.
Test access encryption on independent sites
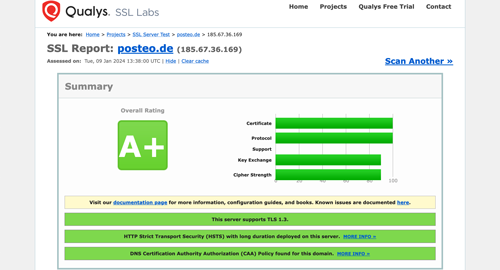
You don’t have to blindly trust us: You can see and test our encryption (as well as that provided by other services) on independent test sites, for example, Qualys. We always keep our encryption up to date. We therefore receive the best possible mark of A+ for the Qualys test (as of 01/2024).
Our extended security certificate
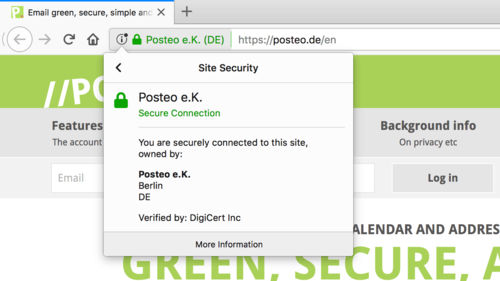
So that you can always be sure that the encrypted connection really is with the Posteo server, we have introduced a so-called extended (green) security certificate, with which you can quickly identify the encryption partner (see image). Such certificates are used first and foremost by companies that have anything to do with sensitive information, for example, banks. In addition, you can also find the fingerprint of our security certificate on the “Impressum” page, in order to perform a manual check.
Why we use an extended certificate
Phishing sites attempt to obtain user data by building identical copies of bank websites and those of other internet services in order to obtain your login information when you log in to a falsified website. With the extended certificate, you can quickly identify that you are really on our website.