New: Posteo migration service now for calendars too
Created on 12. June 2017, 18:00 | Category: Info
Dear Posteo users,
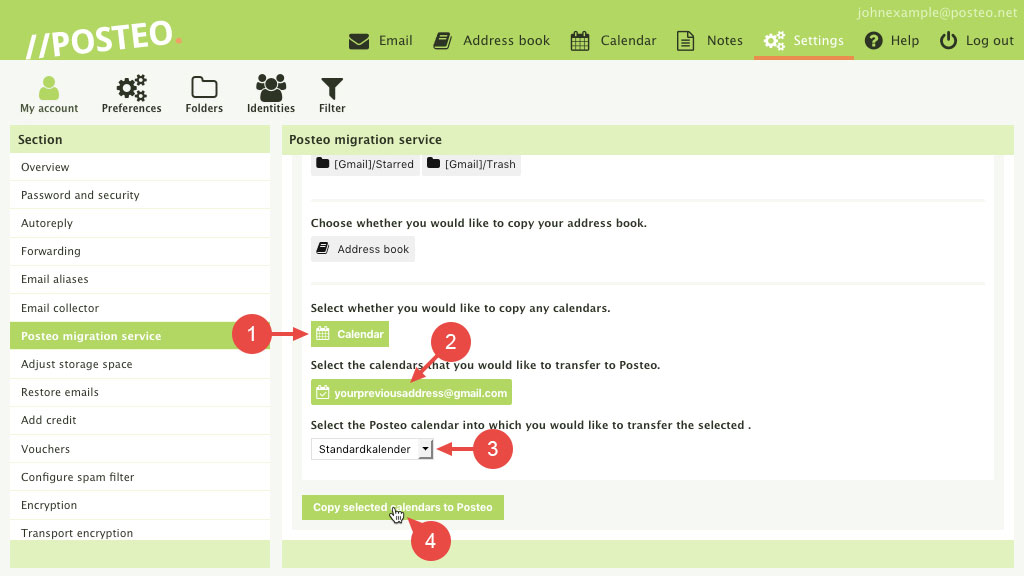
We have extended the Posteo migration service. From now on, you can transfer not only your existing email accounts and address books to Posteo, but also your calendars.
The extended migration service allows calendar transfer from providers such as gmx, web.de, Gmail, Aol or iCloud.
Here’s how it works: You can find the new, extended migration service in the settings of your Posteo account under “My account”. When you undertake a new migration service there, not only the email folders and address book will now be shown to you, but also the calendars from your previous account. With a click of the mouse you can conveniently select which items you wish to transfer to Posteo. You can decide yourself whether to delete the data from your previous provider after the transfer.
Special characteristics of the Posteo migration service:
It is free of charge, you do not require any special technical knowledge for the transfer – and you retain control of your data. We do not use transfer service providers. For this reason, your sensitive emails, address book and calendar data are never transferred over a third-party service at any point. We developed our migration service ourselves, so that it conforms to our high requirements in terms of security and data economy: Your data is collected by us directly from your previous provider and transferred to your Posteo account over encrypted connections.
For reasons of data economy, we also do not save the email addresses from which you have transferred data to your Posteo account, for example.
If you have any questions on transferring your calendar data or the Posteo migration service in general, please feel free to contact Posteo support.
Best regards,
The Posteo team