New at Posteo: Attachment browser with photo stream
Created on 03. September 2020, 12:30 | Category: Info
Dear Posteo customers,
We are releasing a new feature for you: the Posteo attachment browser with integrated photo stream.
The new feature makes your account noticeably more modern and easier to use.
As of this morning, the attachment browser has already been made available to some of you.
In the coming weeks we will gradually make it available for all accounts.
You can then find it in the menu under “Attachments”.
All attachments in a convenient overview
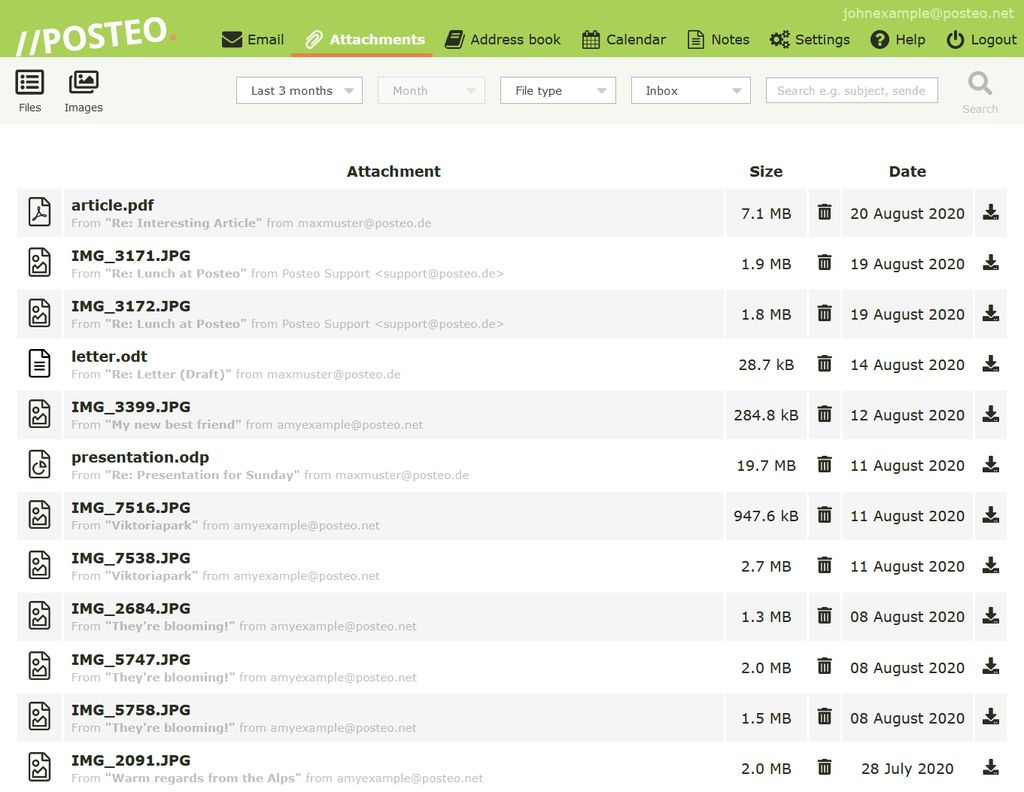
This feature allows you to manage your emails in new ways — attachments are displayed in a separate overview, independent of the corresponding emails. From there you can view, download and delete attachments with ease. Also finding attachments has been made easier. In the attachment browser you can search for files sent from various contacts, at specific times, with specific file names or file types — and combine the search filters. Photos you have received can be found exactly as quickly as contracts or invoices.
The attachment browser makes it easier to work in your own account — while providing you with more convenience and organisation. There is a photo stream available for viewing images.
#more#
Viewing photos in privacy with the photo stream
The new photo stream provides a modern appearance for your account. Photo attachments are visually displayed in a way that might be familiar to you from social media platforms, but remain within the privacy of your email account. The stream can be filtered at your convenience — the photos from your recent vacation can be found as quickly as the photos from the family reunion. Additionally, you can quickly identify which photos you no longer need: a photo can be downloaded or deleted with two clicks.
Delete attachments, save storage space and protect the climate
Many of you requested a separate feature for deleting attachments.
This is now conveniently made possible with the attachment browser at the touch of a button. Attachments that are no longer needed can be deleted while keeping the corresponding email. This frees up storage space and saves resources. Because data saved online continually uses energy. So that you can remember that the deletion occurred, a note summarising which file was deleted as well as the time of deletion is added to the email. This will also be reflected in local email clients and apps.
With the filter option “size” you can quickly obtain an overview of which files and images are taking up a considerable amount of storage space.
You can load the photo stream in the attachment browser via “Images”. In our help section you can find information as well as step-by-step guides for the new feature.
Comprehensive tests and external security check
The attachment browser with photo stream is a Posteo in-house development. We develop ourselves because we have specific requirements for privacy, security and sustainability. For example, as a matter of principle we do not collect any personally related inventory data or traffic data like IP addresses. As a service without advertisements we also refrain from tracking and incorporating social media plug-ins. Because of this, new features are conceptualised so that they effectively continue to not accumulate any personal data in the background. This strengthens your right to informational self-determination — and saves energy resources. Because unnecessary processes, logs and data heaps use a lot of energy.
Your attachments are a sensitive commodity worth protecting: they are subject to telecommunications secrecy and are protected by basic rights. Because of this, your access to your data and its display occur in real time within your account. It is not temporarily saved in databases which is frequently the case with such features. Your data always remains within your account. Also the preview images of the photo stream are not held in databases, but rather generated in real time from your emails as soon as you access the stream. The new feature has been comprehensively tested and additionally checked by independent security researchers (Cure53).
Encryption at the touch of a button
The attachment browser and photo stream are also compatible with our crypto mail storage. If it has been activated, all data saved within the account is encrypted with your password. The new feature is then accessed within the privacy of your own encrypted account. Even we, as the provider, do not have access to your data. This principle can be compared with device encryption on smartphones.
Email attachments that have been sent with end-to-end-encryption (PGP/S/MIME) can not be displayed in the attachment browser.
More updates coming soon
Already in the near future we will be making additional improvements available to you — an optimised version of Posteo webmail for smartphones will also be made available soon. The attachment browser and photo stream have already been customised for mobile use.
Best Regards
The Posteo Team
