New: TLS-receiving guarantee
Created at 25.June 2021, 18:00 | Category: Info
Dear Posteo customers,
We have released a new feature: Our TLS-receiving guarantee.
The new security feature protects you from receiving emails from servers that send them insecurely and rounds off our TLS guarantees: We have been offering a similar guarantee for sending emails for some time now. You can now activate your TLS-receiving guarantee in the settings.
Protection against insecure senders
If you activate the new security feature, we will refuse to receive an email to your mailbox if a server tries to deliver it without up-to-date transport route encryption. An insecure transmission from such servers through the internet is guaranteed to be prevented and you will immediately receive a notification from us. Even as a layman, you can thus immediately recognise who is not making sufficient efforts to ensure email security.
TLS protects your emails on their way through the internet
Nowadays, emails are transmitted via encrypted connections: The transport route encryption (TLS) protects your communication on its way through the internet. Without TLS, emails could simply be intercepted and read in transit. Therefore, almost all email servers now establish encrypted connections with each other as a standard.
The rate of insecure servers without up-to-date TLS encryption is already below 5% (Posteo survey May 2021).
We have tested the new feature both internally and with users over the course of several months. The conclusion: as a rule, the receiving guarantee is not noticed in everyday life, since the vast majority of senders nowadays support up-to-date encryption.
The largest share (>90%) of unencrypted contact attempts is now accounted for by spammers and a few newsletter distributors.
In the rare case that the transmission of a desired email is stopped due to a lack of TLS encryption, you and the sender will immediately receive a notification from us.
Then you have two options:
1. You decide for yourself whether unencrypted transmission is also an option for you in this instance. If so, deactivate the feature for a short time and ask the sender to send it again.
2. You point out the lack of security to the sender; we offer a template for this in our help section. During our field tests, the senders usually reacted within 1-2 working days and activated the missing transport route encryption. Every newly secured server is a contribution to IT security for everyone.
If an operator does not respond or is evasive, you can ask us for assistance at support+tls@posteo.de. We will then also contact the sender for you.
New security check before each email is received
For security reasons, a new TLS check is carried out every time an email is received. This ensures that your emails are not transmitted insecurely even if a server is temporarily not TLS-capable – for example, due to technical problems or an attack.
Transmission is also stopped if unauthorised third parties attack a secure connection and want to force the switch back to an unencrypted connection.
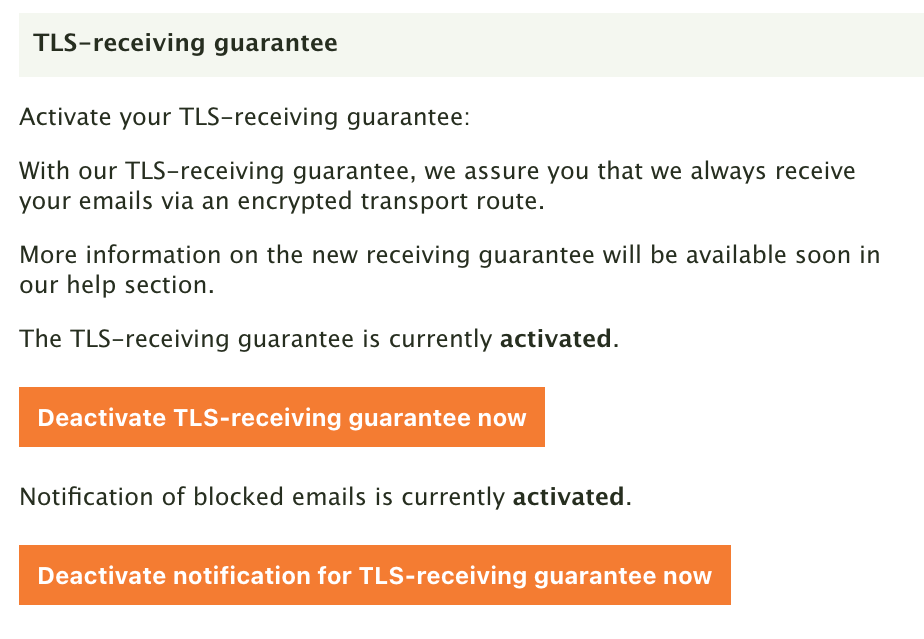
How to activate the TLS-receiving guarantee
You can now activate your TLS-receiving guarantee in the settings of your Posteo account under “Settings → My account → Transport encryption”. Our tip: You can also activate your TLS-sending guarantee there, which we have already been offering for some time.
In our help section, we have provided an article for you on the new TLS-receiving guarantee. With it you will learn how to activate and deactivate the feature – and how to proceed if the transmission of an email from an insecure email server has been stopped.
The TLS-receiving guarantee at a glance:
- Emails are always guaranteed to be received via an encrypted transport route.
- You and the sender will immediately receive a notification if we have stopped the transmission of an email from an insecure server.
- Even as a layman, you can immediately recognise who is not making enough effort to ensure email security.
- Downgrade attacks, in which an attacker can switch off modern, secure encryption, are prevented.
- Outdated encryption protocols such as SSLv3, TLS 1.0 or 1.1 are not tolerated.
- Man-in-the-middle attacks are made more difficult. If, like Posteo, the receiving server uses DANE, they are impossible.
Best regards,
The Posteo Team