Encryption
You need not be at the mercy of large-scale eavesdropping on the internet. Extensive encryption offers reliable protection. Posteo offers a comprehensive and innovative encryption system, that we would like to introduce you to on this page. We apply different methods of encryption at different points.
Posteo always uses the most modern encryption technologies and continually further develops its encryption system. We do everything we can, from our side as a provider, to enhance to the security of your communication. This also depends on some factors over which we have no control. You can also do some things yourself to communicate more securely – we also provide more information on this page.
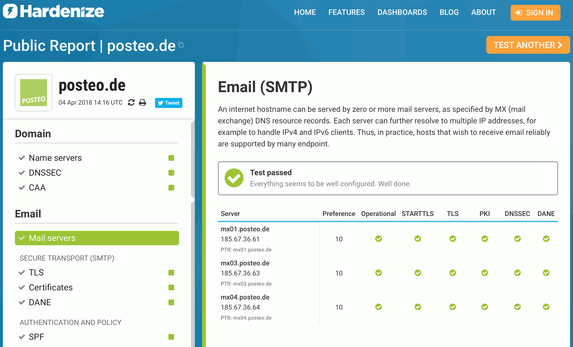
Stay informed: Posteo's encryption concept achieves top marks on various independent test sites such as Qualys SSL Labs and Hardenize.
Overview
Posteo’s encryption layers
Move the mouse over the image or click an encryption layer to learn more about Posteo’s security architecture.
You can find more information on encryption in the following sections:

- Internet: Encrypted connections to other email servers (when possible)
-
Email transport:
Every email that you send to another email provider or server is transmitted by Posteo via an encrypted connection, if the other server supports this. We always use the newest technologies for this.
- TLS (1.0-1.3) with PFS
- DANE/TLSA
Automatic encryption of the transport route occurs in the background, without you doing anything.
It protects:
- The content of your emails
- Their metadata (such as subject, recipient, time)
Further information on transport route encryption at Posteo can be found in the transport route encryption section.
Transparency advice:
The quality of Posteo’s encryption can be tested and viewed on the independent Qualys test site.
- Encrypted access to Posteo is mandatory (website, devices and programs)
-
Access encryption:
At Posteo, all access occurs encrypted.
- Webmail
- Local email programs
- Mobile devices
We do not offer unencrypted access. We always use the newest technologies for access encryption.
- TLS (1.0-1.3) with PFS
- Strict Transport Security (HSTS)
- DANE/TLSA
In addition, we use a so-called extended certificate that enables you to quickly determine that you really are visiting our website.
Further information on Posteo’s access encryption and the extended certificate can be found in the access encryption section.
- Encrypted connections within Posteo
-
Internal connections:
We encrypt all connections within Posteo.
- Encryption using SSH and TLS (among others)
This ensures that eavesdropping occurs neither within the system, nor in the data centre, nor on the way to the backup location.
Further information on encryption within Posteo can be found in the server encryption section.
- Access protection: Password (salted hash)
-
Storage of passwords:
Posteo does not store your password in plain text. Despite this, it is checked with each login using a hash function.
- Passwords do not exist as plain text
- Saved as a salted hash
We do not know your password and can not provide it either to you or to third parties.
Further information on Posteo’s encryption of passwords and mobile phone numbers can be found in the passwords and mobile numbers section.
- Access protection 2 (optional): One-time password
-
Two-factor protection:
With Posteo, you can activate two-factor authentication. This further increases security for access to your Posteo account (in the browser).
Login occurs with:
- Your personal password
- A one-time password
(which changes every 30 seconds)
TOTP process
The one-time password is generated on your device (computer, tablet or smartphone).
Further information on our two-factor authentication can be found in our help section.
- Account protection: Hard disk encryption
-
Server encryption:
All Posteo server hard disks are fully encrypted.
- Linux servers with dm-crypt/LUKS encryption
- Encryption of internal connections (SSH and TLS)
Our encrypted hard disks protect against:
- Hardware theft
- Physical access by unauthorised parties
- Caprice (investigative authorities)
Further information on Posteo’s hard disk encryption can be found in the server encryption section.
- Encryption of all saved emails (optional):
Personalised Posteo crypto mail storage -
Posteo crypto mail storage:
When you activate Posteo crypto mail storage for your account, Posteo encrypts all emails you have saved on our servers.
- Encrypts all email data (content, attachments and metadata) at the click of a button
- The key is protected with your password
- Encrypts all previously saved emails as well as newly-arriving ones
- Asymmetrical encryption with RSA
- Symmetrical encryption and authentication with AES and HMAC, hashing with bcrypt
- Open-source encryption
- External security audit by Cure53
Posteo can not deactivate encryption of your emails. Further information on Posteo crypto mail storage can be found in the crypto mail storage section.
- Posteo inbound encryption (optional):
Encryption of all newly-arriving emails
(with S/MIME or OpenPGP) -
Posteo inbound encryption:
If you use S/MIME or OpenPGP, you can activate Posteo inbound encryption in the settings of your account. This encrypts all newly-arriving emails using S/MIME or OpenPGP.
- Encrypts all newly-arriving emails using S/MIME or OpenPGP, if the sender has not initially encrypted the email.
- Additional protection for your saved emails
Further information on inbound encryption can be found in the end-to-end encryption section.
- End-to-end encryption of individual emails (by the user)
-
End-to-end encryption:
In addition to our measures, you can furnish the content of individual emails with end-to-end encryption. There are two standards for this: S/MIME and OpenPGP (PGP).
- Content of emails is encrypted
- Emails’ metadata (e.g. subject, recipient, sender and time stamp) remain unencrypted
- Sender and integrity of the email can be verified (signature)
- Both communication partners need to use the encryption in order to communicate in an encrypted manner
Further information on end-to-end encryption can be found in the end-to-end encryption section.
- Address book and calendar encryption (optional): Personalised encryption of contacts and calendar entries
-
Address book and calendar encryption:
Posteo users have the ability to encrypt (AES) their calendar and address book data at the click of a button.
- AES encryption directly in the database
- Key protected with your password
- Calendar and address book encryption protects your address book and calendar data from access by third parties
Further information on address book and calendar encryption can be found in the address book and calendar encryption section.
Tip: All of Posteo’s encryption features can be combined with one another without issue.
Access
Access to our server occurs fundamentally over encrypted TLS connections. We secure this additionally with "Perfect Forward Secrecy" technology (PFS) and DANE/TLSA. PFS effectively prevents the possibility that logged connection information could be mass-decrypted by a third party. DANE verifies the authenticity of our server. Thus you can always be certain that nobody is eavesdropping on your network traffic, reading your emails or stealing your access data.
Why we encrypt access:
These days, users access their email through a variety of means – for example, over open Wi-Fi networks or internet cafés. In such circumstances, people don’t only check their email but also log in to other internet sites and services. Because many users have set up similar passwords and usernames with various sites, a door is opened as soon as access to an email account is established.
You don’t have to blindly trust us: You can see and test our encryption (as well as that provided by other services) on the independent Qualys test site. We always keep our encryption up to date. We therefore receive the best possible mark of A+ for the Qualys test (as of 01/2024).
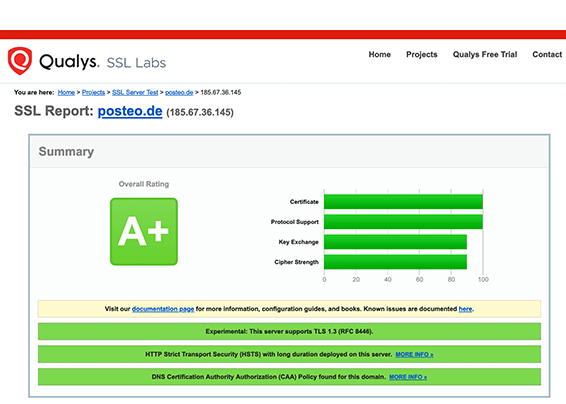
Access to Posteo is always encrypted. We do not offer unencrypted connection.
- Webmail
- Local email programs
- Mobile devices
- TLS (1.2-1.3) with PFS
- Strict Transport Security (HSTS)
- DANE/TLSA
Security tip:
Security tip: Update your browser and email programs at regular intervals. We always use the latest encryption technologies – in some cases, older browsers can not handle this. Internet Explorer 8 does not support the safeguard of encryption with PFS, for example. Like Windows XP support, we no longer provide support for Internet Explorer 8.
Certificate
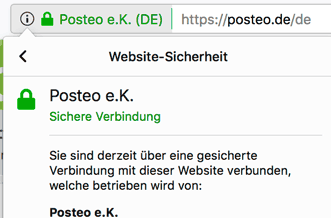
Extended security certificate
So that you can always be sure that the encrypted connection really is with the Posteo server, we have introduced a so-called extended (green) security certificate, with which you can quickly identify the encryption partner (see image). Such certificates are used first and foremost by companies that have anything to do with sensitive information, for example, banks. In addition, you can also find the fingerprint of our security certificate on our legal notice page, in order to perform a manual check.
Why we use an extended certificate:
Phishing sites attempt to obtain user data by building identical copies of bank websites and those of other internet services in order to obtain your login information when you log in to a falsified website. With the advanced certificate, you can quickly identify that you are really on our website.
Transport route
Encrypted email traffic
It’s often said that emails are like postcards in that anyone can read them along the way. This is not always correct. When sending and receiving emails, our servers attempt to establish an encrypted connection (a PFS-backed TLS connection) with the other server. If the other server supports it, the email will be sent via an encrypted connection. This encryption happens automatically in the background; You and your correspondence partner don’t need to do anything more.
If the route is encrypted with TLS, nobody can read the (unencrypted) email on its journey. PFS technology prevents subsequent large-scale decryption by unauthorised third parties. Since May 2014, Posteo also supports the innovative DANE/TLSA technology, which eliminates various weaknesses in the prevalent encryption of email traffic. DANE increases the security when sending emails via an encrypted connection as well as when accessing websites.
Following the NSA scandal, many email services have improved and now support encryption of the transport route, though there are large discrepancies in the quality of the implementation. We hope this will be further improved, as the quality of encryption between two servers depends upon the weaker of the pair. In particular, we hope that the DANE technology that we have taken up will soon become widely used, because we are convinced that DANE significantly contributes to making digital communication more secure. Please take note of the list (on the right), which we regularly update.

- Encryption of the transport route protects all data during delivery from unauthorised eavesdroppers – the content of an email as well as the metadata.
- When Posteo users write to each other, the email exchange does not leave our encrypted servers at any point.
Transport route encryption:
- TLS (1.0-1.3) with PFS
- DANE/TLSA
- Protects emails and metadata
- Happens automatically

TLS: An overview of providers
Encrypted transport route
from Posteo to:
| TLS | DANE | |
|---|---|---|
| Arcor | yes | no |
| AOL | yes | no |
| Bund.de | yes | yes |
| Comcast/Xfinity | yes | yes |
| Freenet | yes | yes |
| Gmail | yes | no |
| GMX | yes | yes |
| Microsoft 365 | yes | no* |
| O2 | yes | no |
| Outlook.com | yes | no |
| Riseup | yes | yes |
| T-Online | yes | no |
| Vodafone | yes | no |
| web.de | yes | yes |
| Yahoo | yes | no |
*DANE is already supported when sending emails from Microsoft 365 to Posteo. According to Microsoft, inbound DANE support is planned for March 2024.
As of 6/2023
Servers
Encrypted servers
Our servers (Linux) are located in a data centre in Frankfurt, Germany. Employees at the data centre have no access to our systems. The hard disks of all Posteo servers are fully encrypted. We use dm-crypt/LUKS to encrypt the hard disks. Encryption and decryption is supported by the CPUs and therefore functions more efficiently (AES-NI).
If the hard disks are disconnected from our servers (due to maintenance or arbitrarily) then the information saved there is not readable by third parties. Even a loss of complete systems would not be a problem in this regard – only we can unlock the information.
We encrypt all connections – including within Posteo: All services used are internally encrypted (with SSH and TLS, among others) so that eavesdropping is not possible either in the data centre or on the way to the backup location.

Your emails are stored on our encrypted hard disks. You can fully encrypt the emails themselves by activating Posteo crypto mail storage.

Server encryption:
- Linux servers with dm-crypt/LUKS encryption
- Encryption of internal connections with SSH and TLS
Features:
- Encrypted hard disks protect against theft and caprice
- Encrypted connections within Posteo’s systems constitute additional protection against unauthorised parties
Crypto mail storage
Posteo crypto mail storage
With Posteo, you have the possibility to encrypt all the email data in your account at the click of a button. The encryption encompasses not only the content and attachments for all emails, but also the corresponding metadata (email header, sender, recipient, time, subject, etc.).
The encryption is comprehensive: it encompasses your email archive saved with Posteo as well as all newly-arriving emails. The data encrypted within crypto mail storage is also no longer readable by us as the provider. The encryption works without you needing to do anything special. Whenever you access an email, it is made readable (only for you) in the background using your password at the moment of access.
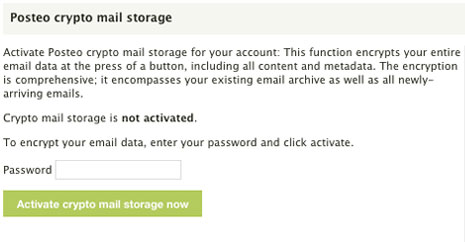
Here’s how:
You can activate crypto mail storage in the settings at the click of a button. You do not need any special technical knowledge. Posteo subsequently generates an individualised key pair for you and encrypts all your email data (content and metadata) in the background. This occurs with the part of your key pair that is responsible for encrypting. The key that makes your emails readable is stored in our database, protected by your personal password. In this way, only you can access your encrypted email storage. With crypto mail storage enabled, your emails will only be decrypted for you the moment they are accessed.
Important:
When you use crypto mail storage, you need to take special care with your password. It is the key to your data. If you forget your password, you will no longer have access to your emails. Changing your password is not a problem: the key to making your emails readable is protected by your new password after the change.
Background information:
Crypto mail storage is a plug-in we developed for the open-source email server Dovecot. Asymmetrical encryption occurs with the help of RSA; symmetrical encryption and authentication are implemented with AES and HMEC. Hashing occurs with the help of bcrypt.
The feature underwent an external, multi-level security audit (by Cure53).
In addition, we had the legal situation clarified beforehand. The result: in Germany, unlike in the UK or the USA, for example, can not be compelled to “break” encryption. We have implemented our crypto mail storage such that from a technical standpoint, the encryption initiated by Posteo users can not be removed by Posteo. In addition, the code for the encryption is openly viewable for reasons of transparency. This conforms to our open-source strategy and is an essential trust-building measure in the post-Snowden era.
Crypto mail storage:
- Encrypts all email data (content, attachments and metadata) including your notes, at the click of a button
- The key is protected with your password
- Encryption encompasses all existing saved emails as well as all newly-arriving emails
- Posteo can not deactivate crypto mail storage
- Can be combined with Posteo inbound encryption as well as encryption of the address book and calendar
Technical details:
- An email encryption plug-in developed by Posteo for the open-source email server Dovecot
- External security audit by Cure53
- Asymmetrical encryption using RSA
- Symmetrical encryption and authentication using AES and HMAC, hashing with bcrypt
Additional information:
Posteo crypto mail storage on GitHub

Because the emails are first encrypted when they reach our servers, Posteo crypto mail storage is no substitute for regular end-to-end encryption set up by the sender of an email. This does not, therefore, protect you from a lawful interception (TKÜ).
Calendar & address book
Posteo users have the option to encrypt their calendar and address book data with their password (AES).
The encrypted data is then no longer readable, even by us as the service provider. Also with encryption activated you can continue to synchronise your data as usual with external clients. The encryption works without you needing to anything special, whether you work in the Posteo webmail interface or synchronise with various programs or devices. Whenever you access your address book or calendar data, it is encrypted with your password at the moment of access. If you change or edit details (of your contacts or calendar entries) these are decrypted and encrypted with your password only at the instant the change is made.
For this solution we use AES encryption directly within our database. When you activate encryption, a random key will be generated, with which your information is encrypted and decrypted. The key is protected by your personal password. If you change your password, the key will be protected by your new password. The information does not need to be encrypted anew. The key is only exchanged when you activate or deactivate encryption. The information is thereby encrypted afresh, in a process that can take a moment.
Accessing the calendar and address book occurs fundamentally with encryption, (i.e. across all devices and email clients).
Important:
If you use calendar and address book encryption, you need to take care with your password. It is the key to your data. If you forget your password, and reset it, you will lose access to your contacts and calendar entries. Our system preserves your data in a container. You can always retrieve your data but only if you later remember your password.
Calendar and address book encryption:
- AES encryption directly in the database
- The key is your password
Merkmale:
- Calendar and address book encryption protects your contacts and calendar entries from access by third parties.

Password & sensitive data

Saving passwords
We do not save your password as plain text. Despite this, it is checked each time you log in using a hash function. Hashing means that from a sequence of characters (your password), a mathematical function computes another sequence of characters (the hash). The result of this process, the hash value, can not be used to derive the password. But your password produces the same hash value each time, as the same function is used to generate it. When you log in, our system generates the hash value from the password entered and compares it with the hash value saved in our database. If the saved hash and the generated one match, you are logged in.
We therefore do not know your password, and can not provide it to you or anyone else.
Saving passwords
- Passwords, mobile numbers and alternative email addresses are not saved at Posteo
- Only salted hashes are stored in our database
Problem:
There is a problem with hashing. Worldwide, relatively few mathematical functions are used to generate hashes, for example, because the result of the calculation should always have the same length (i.e. independent of the length of the password from which it is generated). They generate hashes in advance from many passwords (millions) and save them along with each password. Such a password-hash table is known as a “rainbow table”. In this table you can see which hash corresponds with which password.
Salting:
So that neither we – nor potential criminals – can simply access your password using a rainbow table, we “salt” the passwords. Our system generates a random string of characters for each user (the salt). This happens at the instant you save a new password for Posteo. This string of characters is attached to your password. Then, a hash value is generated from the compound password (your password plus our salt). With each login, we combine your password with the same salt such that the hash value is always the same as the first time. The rainbow table possessed by attackers is thereby rendered useless and has to be newly generated, as each password on the list with the added salt has to be hashed again. Because we allocate a different salt to each user, an individual rainbow table would need to be generated for every single user. This is a huge hurdle which constitutes effective protection of your password.
Encryption of mobile phone numbers and alternative email addresses
When you use our forgotten password feature, the mobile phone number or the alternative email address you enter is also not saved in our system. It only exists there as a salted hash. Despite this, you can request a new password via SMS or email, if you have forgotten it. Click “Forgotten password” and enter your mobile number or your alternative email address. The system holds your number or alternative email address briefly in its active memory, hashes it anew and compares the result with the value that is stored for the password reset. If the hash values correspond, the system resets your password and sends you an SMS to the number or a message to email address just entered. The number or alternative email address, which is briefly used in temporary memory for comparing hash values and sending a password reset, is also deleted at that same moment.
Neither your mobile number nor your alternative email address are saved in our database at any point.
End-to-end encryption
Personal end-to-end encryption
On this page we have presented numerous encryption measures, which we as provider use to protect your data as best as possible. In addition to our measures, you can also become active yourself – securing your emails' content using personal end-to-end encryption. Previously, a local email program such as Thunderbird or Outlook was required for this. With Posteo, meanwhile, you can conveniently use end-to-end encryption (with OpenPGP) in the browser.
How an email is encrypted:
For end-to-end encryption, you require a "personalised encryption code". This consists of two parts and is therefore known as a "key pair". Using one part of the key pair – the "public key" – emails to you can be encoded before being sent. The email is encrypted for its entire journey: It is transferred with encryption from the sender's device to their provider, which then sends the encrypted email over the internet to your provider, which in turn delivers the encrypted email to your account. The email is first decrypted locally, by you, on your device.
At the providers, it is saved encrypted: It is stored with encryption in the sender's "sent" folder and is also encrypted in your account.
How an email is decrypted:
Your contacts only possess your "public key", with which emails to you can be encrypted. The part of your encryption code that makes encrypted emails readable is the so-called "private key". As the name suggests, this is private: For security reasons, it is only located on your personal devices (computer, tablet or smartphone). When you click on an encrypted email, it is made readable on your device using your private key. Never transfer your "private key" to another person, therefore. Also, never save it on a provider's server or in cloud storage. Only thus is the security of your end-to-end encryption guaranteed.
Sharing your "public key" is, on the other hand, specifically recommended: With it, your contacts can encrypt emails to you. Send your public key to your contacts as an attachment to your emails or store it via the settings of your account for others to access in the Posteo public key directory.
S/MIME and OpenPGP: End-to-end encryption technology
There are two standards for end-to-end encryption: S/MIME and OpenPGP. Both of these standards have been able to be used with any email provider for many years. With S/MIME or OpenPGP, you can encrypt or receive individual emails with encryption.
What you need to know:
Both communication partners (sender and recipient) need to have installed the same kind of encryption. S/MIME and PGP are incompatible with each other.
Anonymity
Communication with S/MIME and PGP is not always anonymous. This depends on which S/MIME certificate you use, or how you use OpenPGP.
There are various types of S/MIME certificates:
- Email address: The certificate contains the verified email address of the sender.
- Individual: The certificate contains the verified email address as well as the name of the sender.
- Organization: The certificate contains the sender's company information.
- Sponsor: The certificate contains the sender's verified email address as well as their name and company information.
PGP key servers
If you use PGP, you have no influence over whether your communication partners store your public key on one of the worldwide key servers. There, as well as the corresponding email address, people can see which communication partners have trusted one another. Thus it is possible for anyone to determine who you have exchanged keys with "in trust". It reads similarly to a friend list in social networks. In addition, the email addresses stored can be misused, by spammers, for example.
It is not possible for you to delete your key from these key servers, even if you did not submit it yourself.
The Posteo key directory does not exhibit any of the key servers' weaknesses.
End-to-end encryption also protects against falsified emails:
You can also use a private key to "sign" emails. This confirms that the sender of an email is not falsified – the email standard allows emails to be sent using a fake sender address. This is similar to a letter sent in the post: Any arbitrary sender address can be listed on an envelope.
What a signature does:
- The validity of an email can be checked by the recipient using the sender's public key.
- A signature can also rule out the possibility that the content of an email was manipulated after being sent, similar to a wax seal on an envelope.
- Email clients verify the validity of S/MIME signatures and display whether the sending address of the email is authentic and if the contents of the email have not been altered. Posteo also checks S/MIME signatures and displays the result.
It protects:
- Email content (text and any attachments) in your account
- Email content (text and any attachments) in your communication partner's account
- Email content (text and any attachments) during transfer to the recipient
It does not protect:
- Email metadata (such as the date, time, subject line) remain unencrypted

Tip: Combine personalised end-to-end encryption with Posteo crypto mail storage, which at the click of a button encrypts all metadata for the emails saved in your Posteo account.

Tip: We provide step-by-step instructions on setting up and using end-to-end encryption in our help section.

Tip: S/MIME certificates can easily be created in the Posteo account settings.
PGP in Posteo webmail
End-to-end encryption with OpenPGP
In Posteo webmail, you can use genuine end-to-end encryption with OpenPGP using the browser add-on Mailvelope. The era in which such encryption was only possible using a local email program is over. As previously, the encryption occurs locally on your device – in the browser. Your private key, which makes your encrypted emails readable, remains with you at all times. Posteo has been pre-configured for Mailvelope since October 2014. Since then, we have further developed the Posteo webmail interface, such that Posteo users can use Mailvelope even more conveniently.
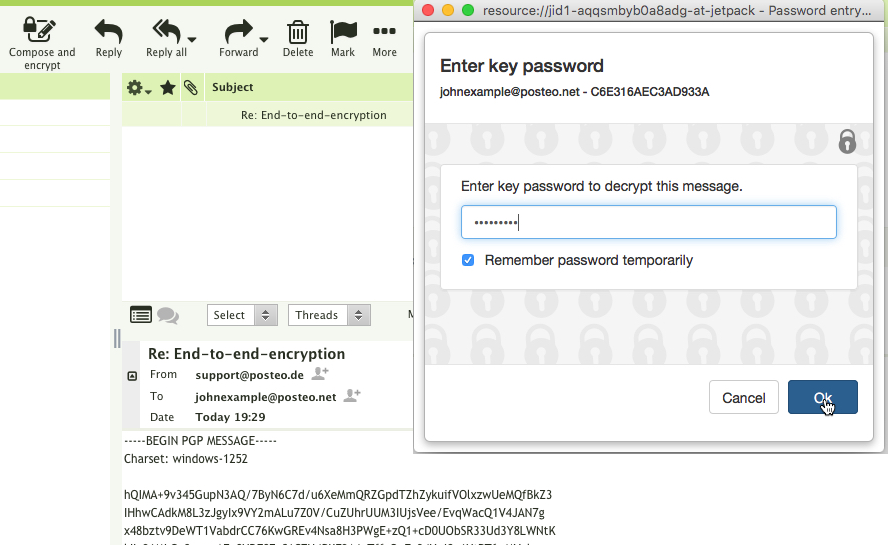
- In Posteo webmail, you can encrypt emails with OpenPGP and send or forward them with encryption.
- Both an email's text and attachments can be encrypted.
- Emails received with encryption can be read in Posteo webmail.
- In many cases, you no longer need to ask your contact for their public key: The Posteo key directory, which is compatible with Mailvelope, can find most publicly available keys automatically. It searches various sources worldwide for keys, and shows you the results. Thus, end-to-end encryption becomes convenient and modern.
Genuine end-to-end encryption is ensured, as your private key always remains locally on your devices. It is not saved on our servers at any point, which would reduce the principle of end-to-end encryption (between the sender and the recipient of an email) to an absurdity. The encryption and key search also work with all other email providers that comply with internationally agreed-upon standards for email. It is not a stand-alone or proprietary solution for which both communication partners would need to be with same provider in order to communicate with encryption.
End to end encryption in Posteo webmail:
- Genuine end to end encryption with OpenPGP and PGP/MIME (for attachments)
- Protects content (text and attachments)
- Available for Firefox and Chrome. Please pay attention to our security advice from May 2017.
- Uses the open-source plug-in Mailvelope, which underwent several security audits
- Worldwide, automatic key search with the Posteo key directory
Posteo key directory
Directory for your PGP or S/MIME keys
If you use end-to-end encryption with Posteo in the browser, in many cases our system can automatically find your contacts' public keys. The Posteo key directory makes this possible – it automatically searches worldwide for keys corresponding to your contacts, and shows you these before you send an email. In many cases you no longer need to ask a contact for their public key before being able to send them an encrypted email.
In addition, you can publish your own public PGP or S/MIME key in the Posteo key directory. Your key is then securely stored in the DNS, the so-called "internet phonebook". There, others can find your key and use it to encrypt emails to you.
We secure the keys in the DNS using innovative technology: Your key is secured against falsification in the Posteo key directory using the soon-to-arrive standards OPENPGPKEY and SMIMEA. This process approximately corresponds to DANE.
By using further security technology such as NSEC3, for example, we prevent the mass-reading of email addresses and keys in the DNS. This actively prevents misuse of the DNS as a source of email addresses for spammers.
In order to publish a public key in the Posteo key directory, it needs to fulfil specific criteria for anonymity: Posteo guidelines for public keys.
In the standard software GnuPG, the new OPENPGPKEY technology is already implemented. Verisign is also working on an SMIMEA plug-in for Thunderbird. For our worldwide key search, we developed an open-source plug-in for Posteo webmail, which is released under the AGPL and can be found on Github.
The Posteo key directory contains:
- Keys published with Posteo
- Keys published in the DNS with other providers
- Public keys that are published on PGP key servers and fulfil specific criteria
Supported applications:
- Posteo webmail with Mailvelope
- GnuPG
- Thunderbird
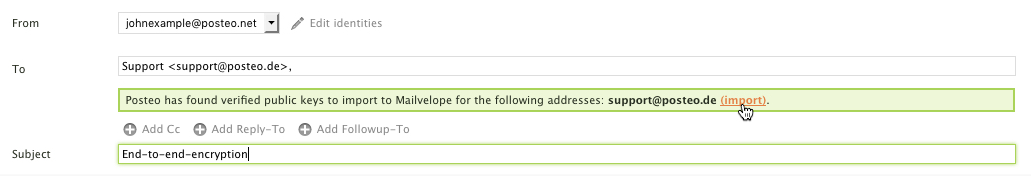
Posteo inbound encryption
Encrypt all inbound emails with PGP or S/MIME
Perhaps you use S/MIME or OpenPGP, but many of your contacts do not. If you would nevertheless like all newly-arriving emails to be encrypted before being saved, you can activate Posteo inbound encryption. Our inbound encryption encrypts all newly-arriving emails with S/MIME or PGP, regardless of whether the sender of an email originally encrypted it or not.
No replacement for complete end-to-end encryption
Inbound encryption constitutes additional protection for your saved emails. As the emails are first encrypted when they reach our servers, however, inbound encryption is no substitute for complete end-to-end encryption implemented by the sender of an email, which protects the email on its way over the internet. It therefore also does not protect you against lawful interception (TKÜ).
Posteo inbound encryption:
- Encrypts the content of all newly-arriving emails using your public S/MIME or PGP key
- Encrypts the content of newly-arriving emails (text and any attachments) in your email account
It does not protect:
- Your email's metadata (such as the date, time or subject line) remain unencrypted
Tip: Combine Posteo inbound encryption with Posteo crypto mail storage, which at the click of a button encrypts all metadata for the emails saved in your account.
Sign up now
Open your Posteo account for 1 EUR per month here, and use it straight away. The signup process does not require you to enter any personal details.
Continue to signup >>